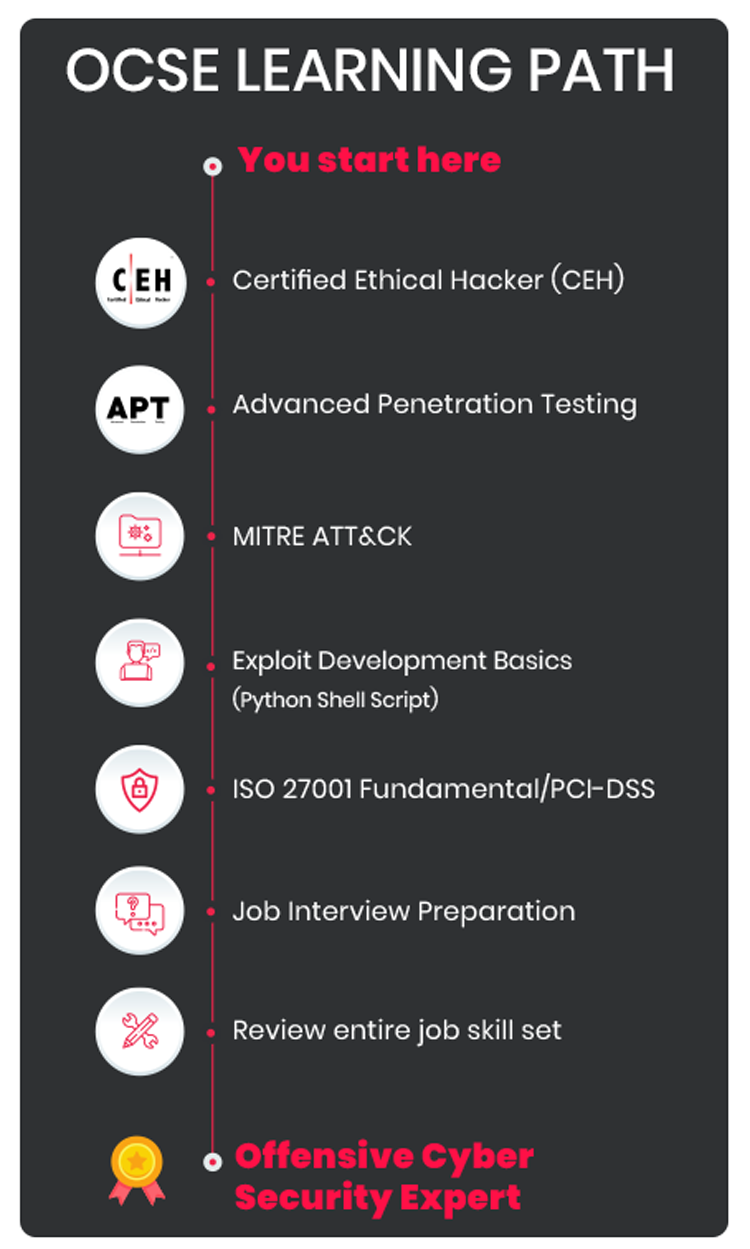
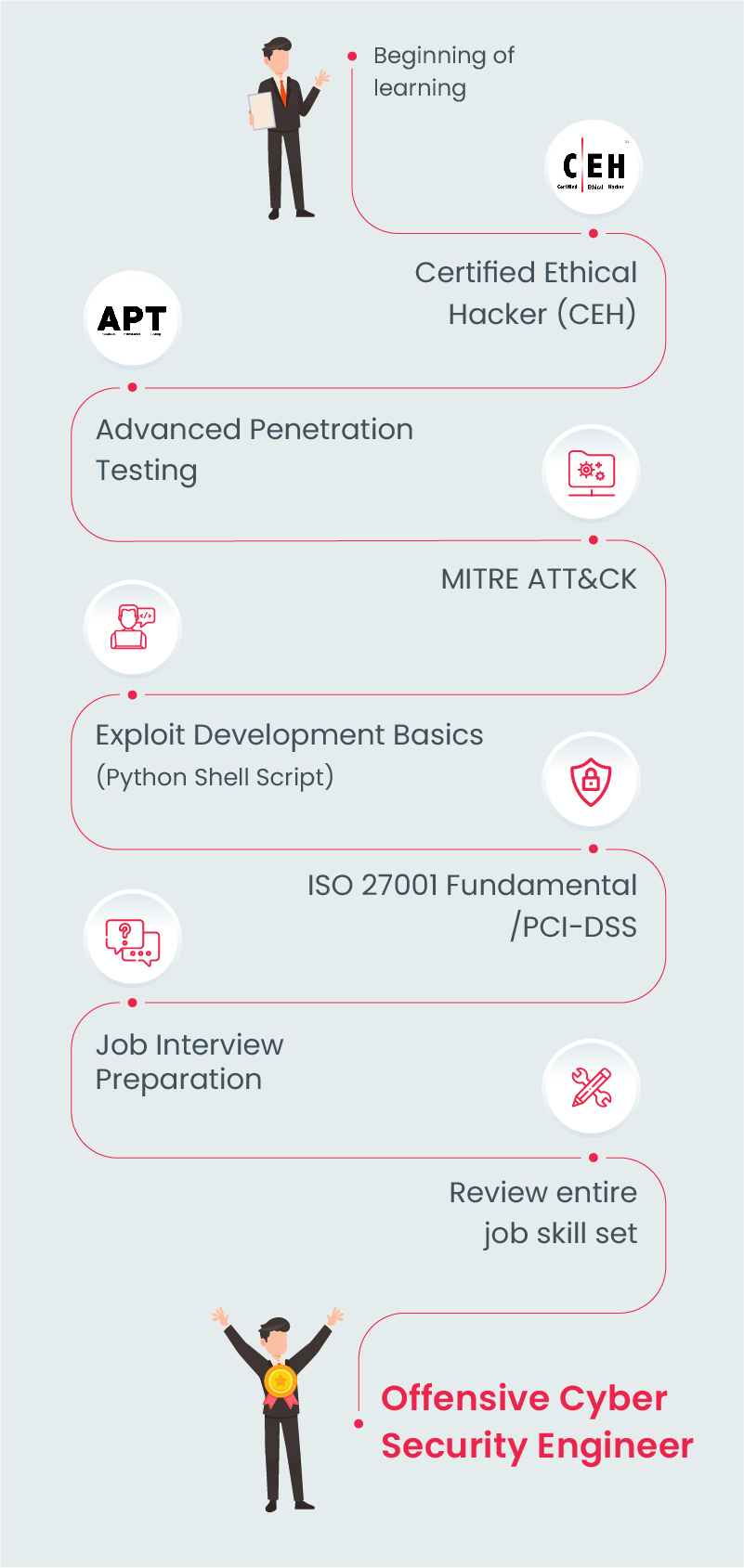
Offensive Cyber Security Course
Offensive Cyber Security Course - Step into the world of ethical hacking and red teams with our offensive cyber security and capture the flag (ctf) course. Matt pearl, director, strategic technologies program. Why the united states government should authorize hack backs. The view that the government should authorize. The exact origins of offensive. Designed for aspiring cybersecurity professionals, this hands. Master offensive cybersecurity tactics with the certified offensive cyber operator (coco) course. General beginners to the field or those looking to transition into offensive security with a focus on windows platforms. National security by defending the department of defense’s networks and critical infrastructure against cyber threats. Learning cyber security on tryhackme is fun and addictive. Offensive security certified professional (oscp). Learning cyber security on tryhackme is fun and addictive. The origins of offensive security. Earn points by answering questions, taking on challenges and maintaining your hacking streak through short lessons. Our courses focus the practical skills needed for penetration testing, web application security, wireless security, and more. Learn about offensive techniques, defensive tactics, cryptography, operating system security, and more. The view that the government should authorize. The oscp (offensive security certified professional) course is one of the world’s most respected and rigorous certifications for ethical hacking and penetration testing. Step into the world of ethical hacking and red teams with our offensive cyber security and capture the flag (ctf) course. Which provides foundational knowledge in cybersecurity. Learning cyber security on tryhackme is fun and addictive. Step into the world of ethical hacking and red teams with our offensive cyber security and capture the flag (ctf) course. General beginners to the field or those looking to transition into offensive security with a focus on windows platforms. Install, configure, utilize, and troubleshoot various offensive cyber security tools and. Why the united states government should authorize hack backs. As the cyber threat landscape continues to evolve,. Master ethical hacking and offensive security principles, covering both basic tutorials and advanced courses for versatile application. Sans offensive operations curriculum offers courses spanning topics ranging from introductory penetration testing and hardware hacking, all the way to advanced exploit. Learn new offensive security. As the cyber threat landscape continues to evolve,. National security by defending the department of defense’s networks and critical infrastructure against cyber threats. Designed for aspiring cybersecurity professionals, this hands. Cyber threats evolve rapidly, and attackers don’t follow textbooks. Transition your career into offensive cyber security course with practical training, industry certification, and job placement. Learn about offensive techniques, defensive tactics, cryptography, operating system security, and more. National security by defending the department of defense’s networks and critical infrastructure against cyber threats. San francisco — the senior director for cyber at the white house’s national security council told an audience thursday that he wants to “destigmatize” offensive cyber. As a customized course registered as part. Cybersecurity from an organizational and societal. Take your skills to the next. Learn about offensive techniques, defensive tactics, cryptography, operating system security, and more. Install, configure, utilize, and troubleshoot various offensive cyber security tools and software for proactive security strategies. The view that the government should authorize. National security by defending the department of defense’s networks and critical infrastructure against cyber threats. Learning cyber security on tryhackme is fun and addictive. Earn points by answering questions, taking on challenges and maintaining your hacking streak through short lessons. The oscp (offensive security certified professional) course is one of the world’s most respected and rigorous certifications for ethical hacking. If you have a career in information security and are intrigued by defensive and offensive techniques, consider becoming an offensive security certified professional (oscp). Matt pearl, director, strategic technologies program. Obtain the critical skills needed to start a career in cybersecurity. Understand the basic principles and. Offensive security can be described as ethical hacking conducted within legal and authorized boundaries. General beginners to the field or those looking to transition into offensive security with a focus on windows platforms. Sans offensive operations curriculum offers courses spanning topics ranging from introductory penetration testing and hardware hacking, all the way to advanced exploit. As the cyber threat landscape continues to evolve,. The view that the government should authorize. Master offensive cybersecurity tactics. Take your skills to the next. If you have a career in information security and are intrigued by defensive and offensive techniques, consider becoming an offensive security certified professional (oscp). Earn points by answering questions, taking on challenges and maintaining your hacking streak through short lessons. The origins of offensive security. Master ethical hacking and offensive security principles, covering both. Understand the basic principles and. Learn about offensive techniques, defensive tactics, cryptography, operating system security, and more. Transition your career into offensive cyber security course with practical training, industry certification, and job placement. San francisco — the senior director for cyber at the white house’s national security council told an audience thursday that he wants to “destigmatize” offensive cyber. Which. Learn how to conduct ethical hacking and penetration testing to identify vulnerabilities. Step into the world of ethical hacking and red teams with our offensive cyber security and capture the flag (ctf) course. Master ethical hacking and offensive security principles, covering both basic tutorials and advanced courses for versatile application. Understand the basic principles and. San francisco — the senior director for cyber at the white house’s national security council told an audience thursday that he wants to “destigmatize” offensive cyber. National security by defending the department of defense’s networks and critical infrastructure against cyber threats. Offensive security certified professional (oscp). Which provides foundational knowledge in cybersecurity. As the cyber threat landscape continues to evolve,. Cyber threats evolve rapidly, and attackers don’t follow textbooks. Obtain the critical skills needed to start a career in cybersecurity. Install, configure, utilize, and troubleshoot various offensive cyber security tools and software for proactive security strategies. Master offensive cybersecurity tactics with the certified offensive cyber operator (coco) course. The origins of offensive security. Take your skills to the next. Offensive security can be described as ethical hacking conducted within legal and authorized boundaries.Certificate in Offensive Cyber Security
Diploma in Offensive Cyber Security
Offensive Cybersecurity The Definitive Guide Security Boulevard
Offensive Cyber Security Engineer Training The Offensive C… Flickr
An Introduction to Offensive Cybersecurity A Webinar The Association
Offensive Cyber Security Engineer (OCSE) Certification Training
Offensive Cyber Security Engineer Training Program OCSE Training
Offensive Cyber Security Engineer Certification Training Cyber
PPT Offensive Cyber Security Engineer Training PowerPoint
An Introduction to Offensive Cybersecurity and Red Team Certification
Learning Cyber Security On Tryhackme Is Fun And Addictive.
Why The United States Government Should Authorize Hack Backs.
As A Customized Course Registered As Part Of Ghabash's Personal Intellectual Property, It Provides An Unparalleled Learning Experience That Is Not Available Elsewhere.
Sans Offensive Operations Curriculum Offers Courses Spanning Topics Ranging From Introductory Penetration Testing And Hardware Hacking, All The Way To Advanced Exploit.
Related Post: